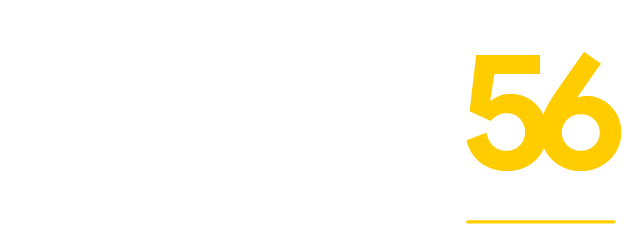Businesses must expand their concept of security and compliance from their own ecosystem. Your partners must have the same protections when you share confidential information with them. Otherwise, you may increase your risk of a customer data breach.
The headlines of cyber attacks that expose consumer data never seem to ebb. Much of the time, these breaches occur as a result of vendor failures. Safeguarding PII (personally identifiable information) and PHI (protected health information) must be a priority, consisting of layers of security and compliance.
Let’s review ways you can keep your company safe. Key to this is choosing the best communication partners with an outlook on data security that matches yours. It’s a necessity, especially for transactional print and mail. If outsourcing is your model or something you’re investigating, ensure due diligence when making your choice.
The State of Customer Data Breach
As customer data breach continues to happen in a world where businesses and consumers rely more on the digital world. Those defending them continue to innovate and establish ways to counter attacks. However, hackers are persistent, scanning for weaknesses that allow them to infiltrate a network.
In 2023, reported cyberattacks reached 2,365, impacting 343,338,964 people. The number of customer data breach was 72% higher in 2023 compared to 2021. PII and PHI are valuable datasets for cybercriminals, which means attempts will rise. Whether or not they are successful is still something you have some control over.
Creating a cyber-secure environment involves a strategy that is proactive rather than reactive. It’s your best chance of ensuring hackers fail. This same vigilance needs to be apparent in your vendor relationships, too.
In transactional print and mail, all communications have PII, PHI, or both. You’ll transmit customer data to this provider. Then, they must keep it safe through the production process and its injection into the mail stream.
Avoiding Risk of Customer Data Breaches in Transactional Communications Partnerships
Choosing to outsource transactional communications yields many benefits. You can reduce costs. You have more options related to dynamic printing. Accuracy and quality can increase, too.
However, many companies are hesitant due to security and compliance concerns. A leading way to have more confidence in this is to work with an organization that only produces transactional mail.
Here are the best ways to evaluate partners that prioritize the security of customer data.
Secure File Processing
Transmitting data to a vendor creates risk and the possibility of a breach. Thus, secure file processing must be robust. Assess the process with an eye on encryption usage, network segmentation, multi-factor authentication, and SFTP (Secure File Transmission Protocol) adoption.
 Continuous Monitoring
Continuous Monitoring
A transactional print company’s network should have tools in place for continuous monitoring. This would consist of advanced firewalls that block unauthorized access attempts. An IPS (Intrusion Prevention System) supports this further by protecting the network at the application layer.
Beyond Compliance Basics
Compliance connects to security. The rules within regulations define many of the things a company must do to protect customer data. Look for a company fully compliant with HIPAA, HITRUST, FISMA, SOCI & II, and PCI DSS. That’s just the first step in evaluating compliance.
You should also seek out companies with:
- A full-time Compliance Officers and staff
- Auditing as part of theirquality assurance (QA) program that could identify any security or compliance gaps
- Intelligent insertion technology and processes to ensure accuracy in mailings
Proactive Cybersecurity Measures
The best communication partners are continuously auditing their security and compliance. They do so with vulnerability assessments and penetration testing. Make sure your provider conducts these regularly. Look for companies that have hired an independent firm to conduct vulnerability and penetration testing so that they get an unbiased based view of their cybersecurity.
Physical Security Considerations
Since print and mail create physical documents with PII or PHI, facilities producing them also need physical security strategies. A customer data breach doesn’t always happen in the virtual world.
To protect against this kind of breach, be sure to review how organizations safeguard data in the physical realm. Some key things to look for include:
- Access-limiting key cards
- Door alarms
- Internal and external security cameras
- Gated entryways
- A secured property perimeter
- Compliant and controlled disposal of documents with PII or PHI
Mitigate Customer Data Breach Risk with PCI Group
We’re a trusted partner for businesses across industries. Since we only produce transactional communications, every aspect of the workflow has security and compliance built in. Enjoy the benefits of outsourcing without the concerns about risk. Learn more by scheduling a consultation with our team.